
Microsoft Compliance Tools - Where Do I Start?
Deeper Dive 4/9: Microsoft Compliance Tools - Where Do I Start? Lois McClintock Explains.
Microsoft has invested considerably in developing compliance tools within the M365 platform. Due to the rapid pace of evolution, many organisations find it overwhelming and are unsure where to begin.
Those who undertake implementation often encounter additional challenges. It is quite common to overcomplicate the process, rendering it difficult to manage and maintain. Furthermore, there is a risk of creating security measures so stringent that they impede employees from performing their duties effectively.
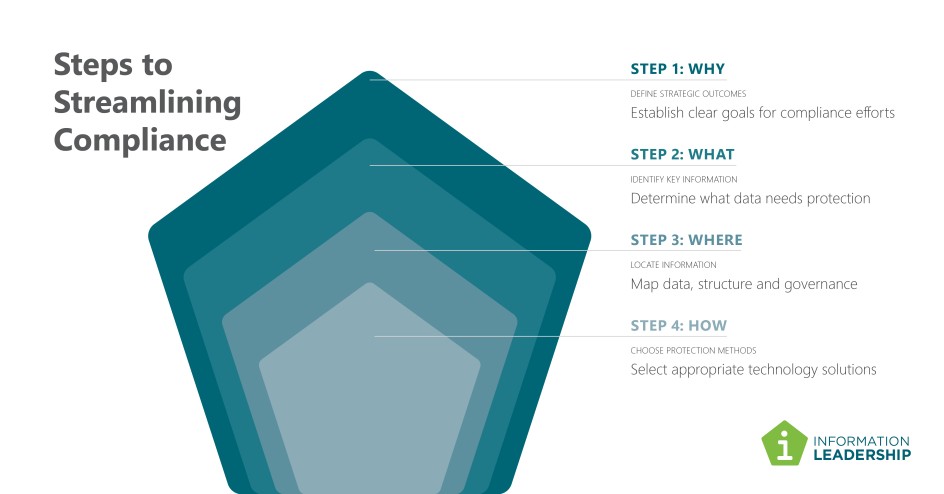
Before exploring all the features and settings, it is essential to step back and define the desired outcomes at a strategic level.
As Simon Sinek suggests, start with “why?”. Organisations have various reasons to protect their information, depending on their industry and location. However, common factors, like privacy requirements, apply to all.
These reasons form the basis for your next steps and can help you communicate the reasons for changes and new process changes to your users later on.
Once these are defined, the next steps are to define your “what?”.
What are the key types of information that need protection? Which ones pose the highest risk to our organisation in the event of a breach or leak?
You don't need to protect everything. Focus on what offers the greatest risk reduction for your organisation. Apply the 80/20 rule: securing 20% of the critical content will mitigate 80% of the risk. Concentrate your efforts there.
After identifying the critical information, it is important to determine “where” this information is located within your organisation. Is there a structured information management system that is utilised by staff? Or is the information scattered across various locations without consistent management or governance?
Well-structured information is the best foundation for effective information protection. It is possible to apply protection methods to a less structured environment, but this is complex to manage and likely expensive as it would require multiple different toolsets to get the job done.
Moving your workloads into the M365 ecosystem allows access to various features in one place. This approach can potentially provide more effective information protection compared to managing a dispersed ecosystem.
Finally, once you have worked through the “why”, “what” and “where”, you can move to the “how” and identify the appropriate technology to do the job. This may also involve moving your information to platforms where it can be better protected.
When protecting information in the M365 arena, it is important to think about a pragmatic layered approach based on your previously identified priorities. No single feature should be used in isolation.
Areas to Focus - Maximising M365 Tooling Efficiency
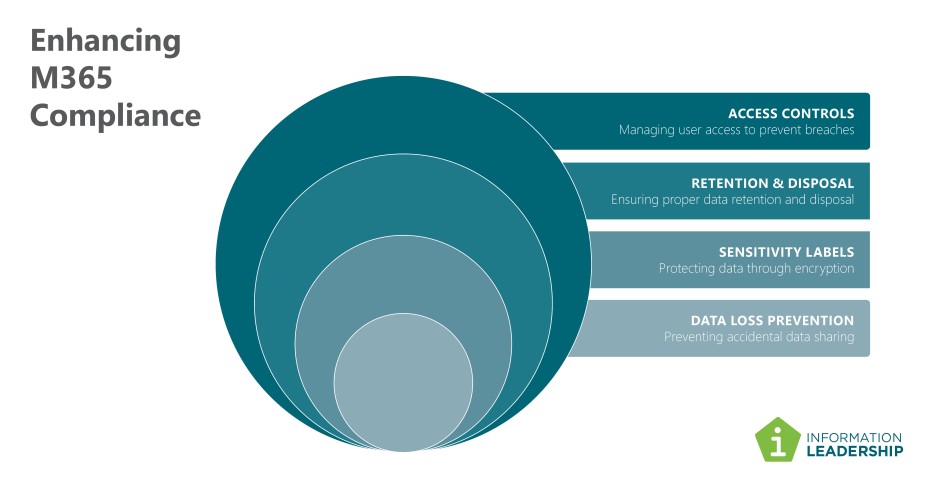
Access Controls and Governance
Many organisations have unmanaged SharePoint sites and Teams containing sensitive information, where users can freely add or remove people, including external parties. This feature is enabled by default in your Microsoft tenant unless settings are changed.
Putting the correct governance and access management in place immediately decreases your risk of an accidental information breach.
Retention and Disposal
Records required for legislative and compliance purposes must be safeguarded against deletion. Conversely, records that should not be retained longer than necessary must be appropriately disposed of. This is particularly crucial when considering privacy data. Retaining information beyond its required period can result in significant repercussions in the event of a data breach.
Microsoft Purview offers excellent options* and detailed control for applying retention labels. While many organisations use broad settings to prevent data loss, a well-planned configuration can better specify retention periods for different types of information.
iWorkplace Smart Labels and Smart Records tooling can deliver a powerful boost to any implementation with its ability to automate the application of Retention Labels at scale.
Sensitivity Labels
Applying well-defined sensitivity labels to critical information is an effective method of protecting data through encryption. It is essential to balance this approach with an operational assessment to ensure that the selected protection measures do not cause any disruption.
There are several effective options available for these labels*. It is important to ensure that the implementation remains straight forward and not confused with information classification. Sensitivity labels are a tool, not a classification. Understanding this distinction helps avoid the compulsion to apply a sensitivity label to every document. This is not necessary.
Data Loss Prevention (DLP)
The DLP configuration* in Microsoft Purview can be effectively utilised alongside sensitivity labels to achieve straight forward and effective outcomes. These features help prevent information accidents by prompting users to consider what they may be sharing or sending externally. Instead of completely blocking these actions, it is often advisable to create a pause for users to reflect on their actions. However, in certain situations, it may be necessary to fully block actions. This should be done with caution, as there is a risk of overlooking critical information use cases even with thorough business process analysis.
*It is important to note that the available feature sets differ between licensing levels. The best feature sets come with the premium licensing types, but that should not prevent you from investigating and exploring your options.
If you’ve read this far, improving information compliance is probably on your priority list for 2025. Start with defining your "why" to understand the reasons behind protecting your information and then work through the other steps to work out the best path forward for your organisation.
By laying a good information management foundation and taking a pragmatic approach to information protection, you can significantly reduce your organisation’s risk profile.
If you’d like help working through this process, get in touch or find out how iWorkplace can help deliver practical information protection and compliance for your organisation.